Green Torque International FZC
27 December 2023
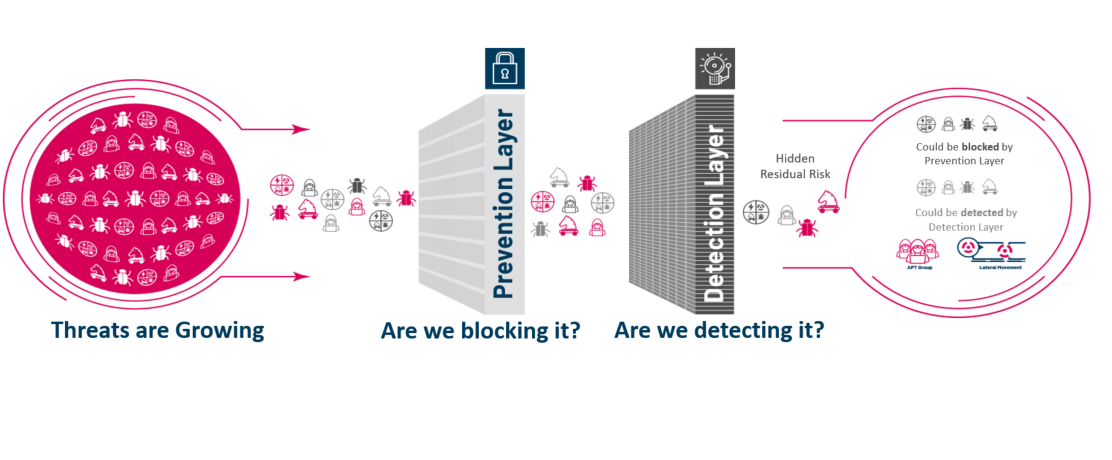
Malicious software can be tremendously impairing, especially to businesses and organisations. Each year, as security measures advance, so do these malwares. Research reveals the rise of sophisticated “Hunter-killer” malware that actively seeks out defensive tools and impairs them to remain stealthy for longer. As malware becomes more advanced and creative with time, it urges users safeguarding sensitive information, to not skimp out on the security and safety of their devices.
Due to this significant need that is ever rising, Green Torque has joined forces with cybersecurity veterans, Picus. The transformative security validation solution for end-to-end attack readiness, visibility, and effortless mitigation to pre-empt cyber-attacks across all cyber defence layers, allows us to gain granular and practical insights.
These insights are provided by simulated attacks, which are based on analysis of over 600,000 malware samples, executed in a safe and controlled environment without hindering or stopping the functioning of your system. This provides us with an understanding of your security control’s efficacy to protect critical assets, which gives us the necessary data to determine vulnerabilities.
Cloud servers also stand to benefit from the insight gained, which paves the path for the identification of misconfigured clouds, preventing overly permissive policies and addressing gaps and risks.
Key Features:
Threat Assessment: Identify potential weaknesses in your security infrastructure through simulated cyberattacks, including phishing, malware, and insider threats.
Vulnerability Analysis: Gain insights into your organization's susceptibility to breaches and prioritize security improvements based on risk assessment.
Incident Response Evaluation: Test the effectiveness of your incident response procedures and refine your response strategy to minimize impact in the event of a breach.
Performance Metrics: Receive detailed reports and metrics to track your security readiness over time and measure the effectiveness of remediation efforts.
Let us to fortify your defences and safeguard your organization's sensitive data. Contact us today to schedule a consultation and take the proactive steps towards enhancing your cybersecurity posture.